Learning how to make SSL on HSHub for Handshake domains
Want to have an SSL on your Handshake site? Like we did for handshake.conference?

Then let’s dive in today!
Many of you enjoyed the video we did with Matt Zipkin on DANE and security (check it out here - 999999 skyinclude.com/dane) - and I feel guilty but most of the sites we have on Handshake still are not secure.
Another reference - is using Cloudways - we have a video on that here - https://skyinclude.com/setup-handshake-domain-names-using-cloudways/
With HandyCon 2 coming in less than 2 weeks, and people asking for it to have SSL - there is perfect timing that I found out the new HShub (you can watch our video and guide at skyinclude.com/hshub) has the ability for your to do SSL.
Check out the Twitter exchange
https://twitter.com/MatthewZipkin/status/1500088996977860610?t=FntE0Le0zQxL-nrvdPPZGg&s=19
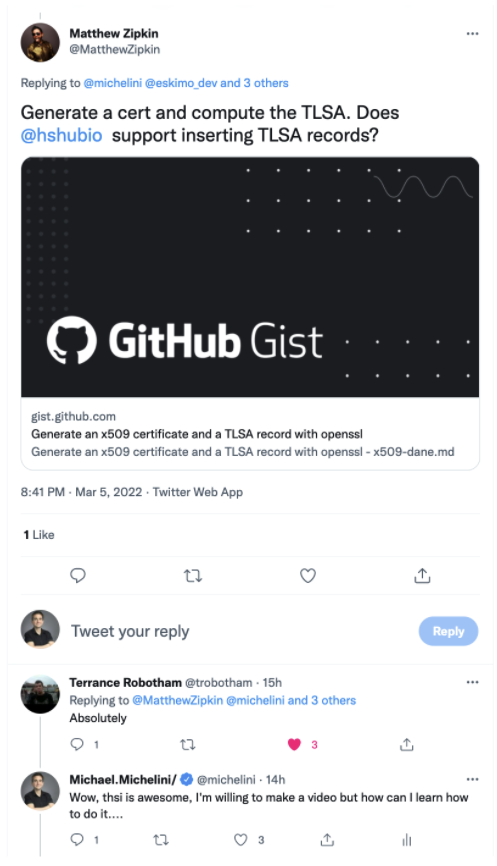
https://gist.github.com/buffrr/609285c952e9cb28f76da168ef8c2ca6
EPIC!
So let’s learn this together. The theme of the SkyInclude channel is coming to life yet again.
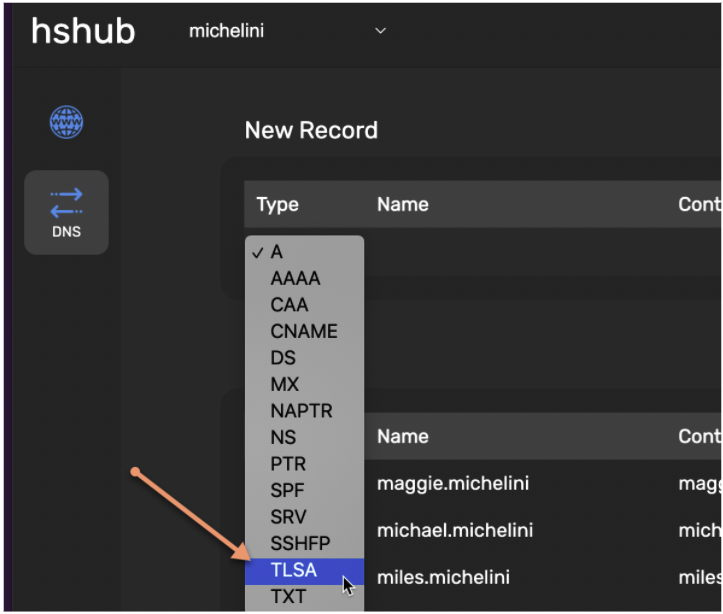
So we need to create the certificate and then add the TSLA record, which HShub supports:
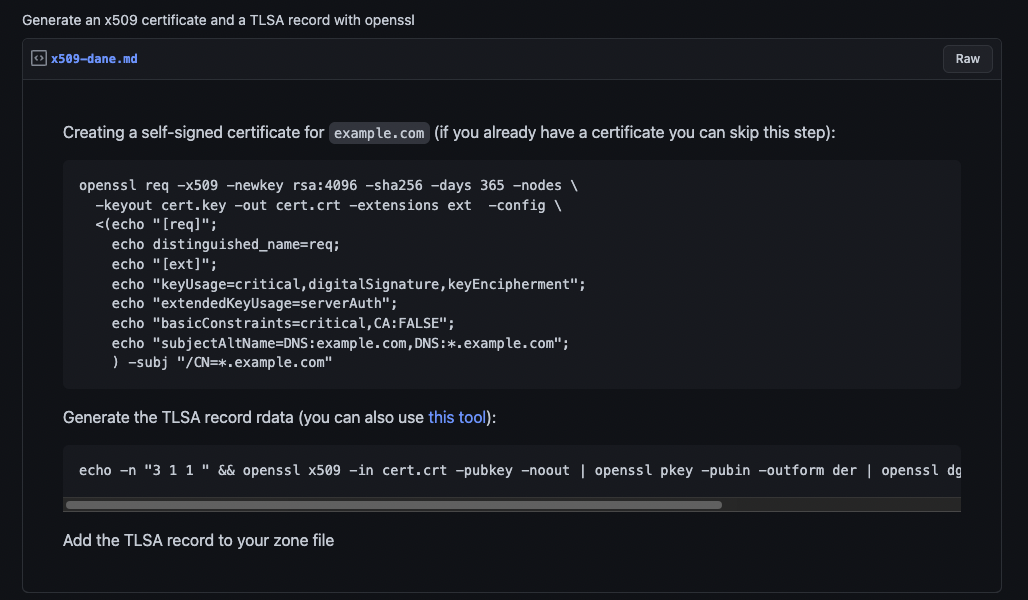
So we need to create this certificate, and following the guide from buffrr: https://gist.github.com/buffrr/609285c952e9cb28f76da168ef8c2ca6
openssl req -x509 -newkey rsa:4096 -sha256 -days 365 -nodes \
-keyout cert.key -out cert.crt -extensions ext -config \
<(echo "[req]";
echo distinguished_name=req;
echo "[ext]";
echo "keyUsage=critical,digitalSignature,keyEncipherment";
echo "extendedKeyUsage=serverAuth";
echo "basicConstraints=critical,CA:FALSE";
echo "subjectAltName=DNS:example.com,DNS:*.example.com";
) -subj "/CN=*.example.com"
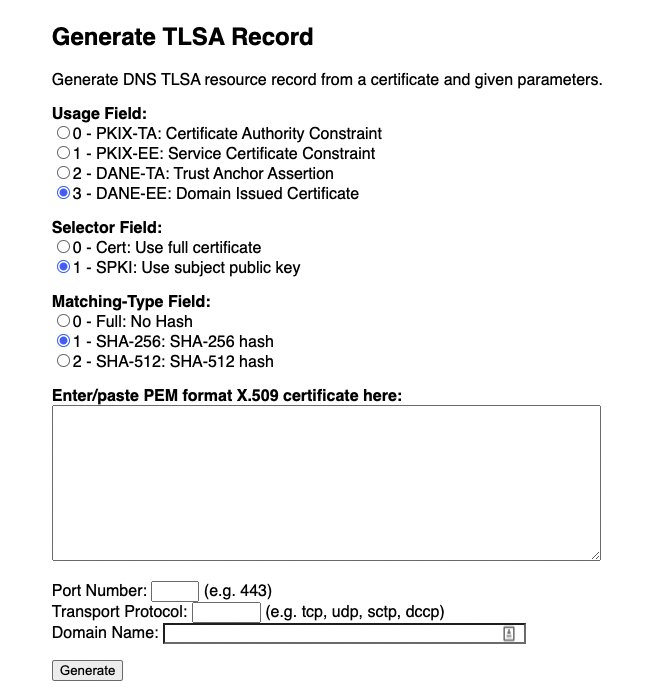
We need to input:
Generate the TLSA record rdata (you can also use this tool):